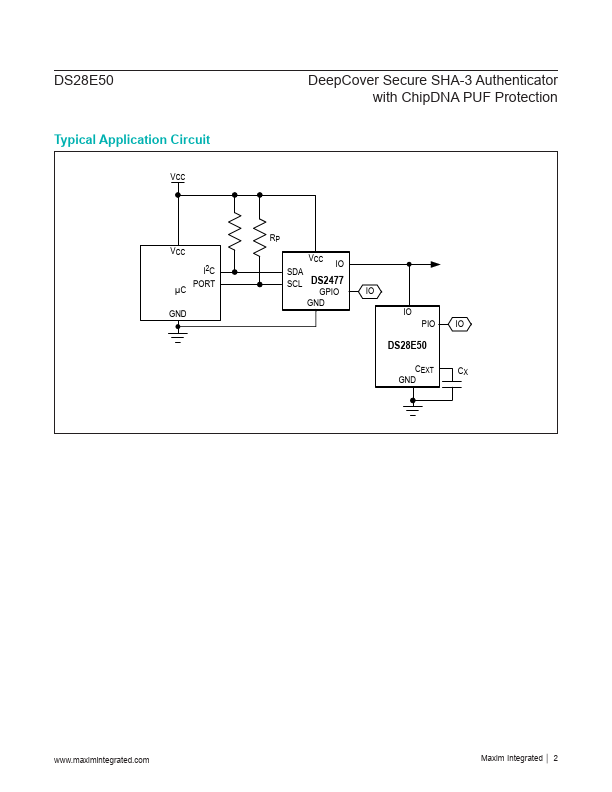
DS28E50 Description
The DS28E50 secure authenticator bines FIPS202pliant secure hash algorithm (SHA-3) challenge and response authentication with Maxim’s patented ChipDNA™ technology, a physically unclonable function (PUF) to provide a cost-effective solution with the ultimate protection against security attacks. The ChipDNA implementation utilizes the random variation of semiconductor device characteristics that naturally occur during...
DS28E50 Key Features
- Robust Countermeasures Protect Against Security Attacks
- Patented Physically Unclonable Function Secures Device Data
- Actively Monitored Die Shield Detects and Reacts to Intrusion Attempts
- All Stored Data Cryptographically Protected from Discovery
- Efficient Secure Hash Algorithm Authenticates Peripherals
- FIPS 202-pliant SHA-3 Algorithm for Challenge/Response Authentication
- FIPS 198-pliant Keyed-Hash Message Authentication Code (HMAC)
- TRNG with NIST SP 800-90B pliant Entropy Source
- Supplemental Features Enable Easy Integration into End